Purchasing a new computer is a big investment. Many small businesses and home PC owners end up struggling with older systems because they want to get as many years out of them as possible.
Have you found yourself banging on your keyboard in frustration? Have you tried every tip and trick you found online, only to still struggle with a slow PC?
There are some promising upgrades you can do that will cost much less than the price of a new computer, while making your PC feel like new again.
Here are some of the options you can try to improve the performance of an older computer.
Upgrade to a Solid-State Drive (SSD)
Prices for solid-state drives have come down quite a bit in the past few years, making them an affordable upgrade that can breathe life back into an older PC that might be slowing down.
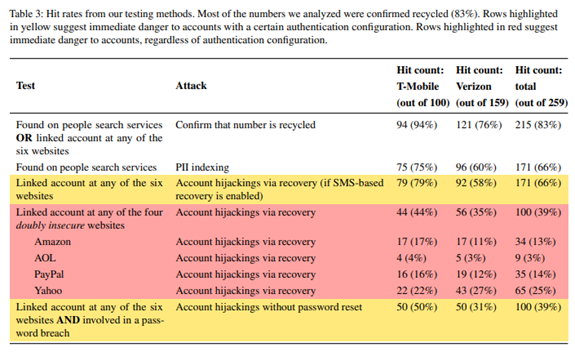
Unlike hard disk drives (HDDs), SSDs do not have any moving parts and use a flash memory that allows for a quicker response time. You can improve your time to boot and your experience when searching files, opening applications, and other activities.
Some of the advantages of upgrading your computer’s hard drive to SSD include:
- SSD read/write speeds up to 2500 MB/second compared to HDD at up to 200 MB/second
- SSD access time of 0.1ms as compared to HDD at 5.5-8.0ms
- SSDs use between 2-5 watts of energy compared to HDD at 6-15 watts
Increase the RAM (Memory)
One upgrade that is very low-cost and can mean a significant increase in performance is a memory upgrade. If your PC was one of the cheaper ones that only had 4GB of RAM when you bought it, you likely have trouble opening too many tabs in your browser or using any graphics-heavy program.
Upgrading your RAM, if your PC has available memory slots, to 8GB or 12GB can make it seem like you have an entirely new computer due to the big increase in speed.
Upgrade the Graphics Card
If you play computer games or work in any type of video, imaging, or 3D software, an outdated graphics card can ruin your experience.
Instead of replacing your entire computer, just upgrading the graphics card to a more robust model can improve your PC’s performance and give you several more useful years from it.
Replace Your PC Cooling System
Heat is an enemy of your computer’s internal parts. If your cooling system is getting worn out and not working the way it should be, then excess heat can be building up inside your device.
When this happens things can get strange, with programs crashing or your system rebooting on its own.
If you suspect excess heat may be an issue, have your computer’s fan and cooling system checked out to see if it needs replacing.
Connect an External Monitor to a Laptop
If you’re working on a laptop and having a hard time multi-tasking due to limited screen real estate, consider getting an external monitor rather than replacing your entire PC.
Monitors are just a fraction of the cost of computers, and having a screen twice the size of the one on your laptop can make all the difference in the world and improve productivity due to the additional screen space.
Replace Your Keyboard
Older keywords can stick, lose keys, and have the writing rubbed off the keys, making it more difficult to tell a “prt screen” from a “delete” button. If the performance of your PC is hampered by a frustrating keyboard, an upgrade can be a very inexpensive way to improve your equipment.
Get an External Hard Drive
Computers can slow down and be more difficult to use when the hard drive fills up with data. Over the years, files build up, and many users never take the time to go through and delete those that are unnecessary.
Buying an external hard drive can allow you to offload files that may be slowing you down, while still keeping them easily accessible.
Another benefit of an external hard drive is that it’s portable and can easily be carried between home and work and used in both places.
Get a Professional Computer Tune-Up
Those free PC cleaner tools you find online aren’t going to give you the type of tune-up that a professional IT provider can give. We will go through things like the Windows Registry, duplicate system files, internal errors, and more to clean up your system and remove all the “junk” that has built up over the years.
We can also do a maintenance check for things like failing parts, and provide expert guidance on your most impactful upgrade options.
Get Help Improving Your Computer’s Performance Today!
Don’t struggle with an older PC! We can help you with cost-effective upgrade options that will fit your system and budget perfectly.
This Article has been Republished with Permission from The Technology Press.